Do this.
Do that.
If the grass is purple, do a somersault;
Otherwise, do jumping jacks.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
F H J L N P R T V X Z B D G I K M O Q S U W Y A C E
V TIKN CIU NGXIC DFST JFDK!
| 1 | = | 100 |
| 10 | = | 101 |
| 100 | = | 102 |
| 1/10 | = | 10-1 |
| 1/100 | = | 10-2 |
| 23579 | = | (2 x 104) + (3 x 103) + (5 x 102) + (7 x 101) + (9 x 100) |
| = | 20000 + 3000 + 500 + 70 + 9 |
| 2.3849 | = | (2 x 100) + (3 x 10-1) + (8 x 10-2) + (4 x 10-3) + (9 x 10-4) |
| = | 2 + 0.3 + 0.08 + 0.004 + 0.0009. |
| 1 | = | 1 x 20 = 1 (base 10) |
| 10 | = | (1 x 21) + (1 x 20) = 2 + 0 = 2 (base 10) |
| 11 | = | (1 x 21) + (1 x 20) = 3 (base 10) |
| 100 | = | (1 x 22) + (0 x 21) + (0 x 20) = 4 (base 10) |
| 101 | = | (1 x 22) + (0 x 21) + (1 x 20) = 5 base 10). |

| 0 + 1 | = | 1 (mod 2) |
| 1 + 1 | = | 2 = 0 (mod 2) |
| 11 + 1 | = | 100 = 0 (mod 2) |
| 1 + 1 + 1 | = | 11 = 1 (mod 2) |
| + (mod 2) | 0 | 1 |
|---|---|---|
| 0 | 0 | 1 |
| 1 | 1 | 0 |
base, prime, my-number, your-number, and key. To let StarLogo know that we will be using these variables, on the first line of the Procedures window type
globals [base prime my-number your-number key]setbase, setprime, and so on, which we will be using. To begin our first procedure, type
|
|
make-key. First it sets the value of the variable prime to 9972. Next it sets the value of the variable base to 281. When we come to the next line, you should replace 11 with another number of your choosing. A good number would be between 2 and 20. For the time being you can leave the value of your-number at 28118. When you actually encrypt or decrypt a picture, you will need to be told this number by the person you are sending the picture to or receiving the picture from. On the next line, the command (your-number ^ my-number) tells StarLogo to compute your-numbermy-number. The command mod then takes this number modulo prime. The result of this entire computation is the value assigned to key.
bitxor. We will be using it soon.
key mod 256, the value of our key (in base 10) modulo 256, we will find the base 10 value of the first eight-binary-digit chunk of the key.
int (base / prime). If we compute this, we have essentially cut off the first eight digits of the binary form of the key. Now if we take this new number modulo p, we will have found the second chunk of the key. We can repeat this process as long as there are chunks of key left to find the value of.
to make-key-turtles
if not (key = 0)
[crt 1
osetc-of (count-turtles - 1) (key mod 256)
setkey (int (key / 256))
make-key-turtles]
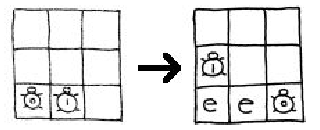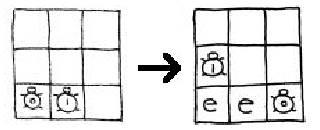
endif statement is for. The expression not (key = 0) is called a conditional statement; it is either true or false. If it is true, then the commands enclosed in square brackets are run. If the conditional statement is false, then the commands in square brackets are ignored. That is, the if statement tells the computer to run some commands only if the conditional statement is true. One of the commands that gets ignored if the conditional statement is false is make-key-turtles, which calls the procedure again, so we check to see that there are still blocks left in the key before trying to call the procedure again.
crt 1 stands for create-turtles 1, which tells StarLogo to create one turtle. Each turtle is numbered as it is created, with the first turtle having the ID number 0, the second turtle having the ID number 1, and so on. The command osetc-of (count-turtles - 1) (key mod 256) tells StarLogo that we want to set the color of the most recent turtle (the turtle with ID number one less than the total number of turtles created so far) to the value key mod 256. Recall that this is the value in base 10 of the first chunk of the key. The next line cuts this first chunk off of the key. Now when we call this function again, if we still have chunks of the key left to process then it will create a new turtle that will have as its color the value of the next chunk in the key.
to encrypt
repeat stop-after
[setxy counter-x counter-y
setcounter 0
repeat (min count-turtles patches-left)
[setx-of counter (counter-x + counter)
if ((counter-x + counter) > screen-edge)
[sety-of counter (counter-y + 1)
setx-of counter ((counter-x + counter) - screen-size)]
setcounter (1 + counter)
wait 0.1]
stamp (pc bitxor color)
setcounter-x (1 + xcor-of (counter - 1))
setcounter-y (ycor-of (counter - 1))
if (counter-x > screen-size)
[setcounter-x (counter-x - screen-size)
setcounter-y (1 + counter-y)]
setpatches-left (patches-left - counter)]
endrepeat tells StarLogo that we want to repeat a set of instructions multiple times. The exact number of times that we will repeat this loop is the value of stop-after, a global variable that we will need to declare and set the value of. During each iteration of this loop, the turtles will be performing one batch of encryptions.
counter-x and counter-y, which are also global variables that we will need to declare and set the values of. Once all of the turtles are on this base patch, we want to move individual turtles to their correct positions. This will be done in the next loop.
repeat loop, notice that we are setting the value of the variable counter to 0. counter is a global variable that we will be using within this next loop, so we will have to declare counter.
count-turtles number of turtles that we need to make sure get to the proper patches, so we will be repeating this loop count-turtles number of times.(5) Within this loop we use the if statement again. We also use the commands setx-of and sety-of, which set the x and y positions, respectively, of the turtle with the given ID number. The last command, wait 0.1, tells StarLogo to pause a moment before carrying out any more instructions. This allows us to see the turtles as they move. If we remove this command, the turtles would whiz along the screen very fast (try this once you have the entire program working!).
stamp (pc bitxor color). The command stamp tells StarLogo that each turtle should set the color of the patch that it is on to the color immediately following the command. The color that we want each turtle to set its patch to is computed in (pc bitxor color): pc gives the color of a turtle's patch, and color gives the turtle's own color.
counter-x and counter-y, the variables that tell the turtles what base patch they are beginning their encryption at. We want to set the values of these variables equal to the x and y position of the first unencrypted patch.
stamp command do this?
encrypt, we used a bunch of global variables that we still need to declare and to give initial values to. To declare these variables, return to the top of the Procedures window. On the line immediately below the previous variable declaration, type the following line.
globals [stop-after counter-x counter-y counter patches-left]
to reset
setcounter-x (0 - screen-edge)
setcounter-y (0 - screen-edge)
setpatches-left (screen-size * screen-size)
ifelse ((patches-left / count-turtles) - int (patches-left / count-turtles)) = 0
[setstop-after (patches-left / count-turtles)]
[setstop-after (1 + int (patches-left / count-turtles))]
endscreen-edge, -screen-edge) (the top right corner has position (screen-edge, screen-edge)). The number of patches to a side is screen-size, which is equal to 2 times screen-edge + 1 (for the position 0), and the picture is a square, so the total number of patches is screen-size * screen-size. All of them are unencrypted before we start.
patches-left / count-turtles minus the largest whole number less than it is zero (which would be the case if the number of turtles evenly divided the number of patches). If this is the case, then we can stop repeating after that many times. If not, we have to add one to the largest whole number less than the number of patches divided by the number of turtles to find the number of batches to run.
encrypt procedure by adding a line to call the reset procedure at the beginning. The beginning of the modified encrypt procedure will then look like this.
to encrypt
reset
repeat stop-after
endencrypt. We can make another new procedure, setup, which calls the first two procedures that we made. We may also want to make sure that the Graphics window is clear when we begin. This can be done by telling StarLogo to ca, or clear all.
to setup
ca
make-key
make-key-turtles
endsetup. if the name of the button and the name of the procedure are different, click on the circle next to Show Name to make sure that the name of the button will appear on the button. Now click OK, and the button will appear in the Interface window.
encrypt procedure. This procedure will actually both encrypt and decrypt pictures (try this!), so you might want to give this second button a name that indicates that.
setup button, you can import your picture back into the Graphics window by choosing Import from the File menu. You can also import your friends' pictures to decrypt. If you are encrypting your own picture, be sure to export it again after it has been encrypted!
globals [base prime my-number your-number key]
globals [stop-after counter-x counter-y counter patches-left]
to make-key
setprime 9973
setbase 281
setmy-number 11
setyour-number ((281 ^ 18) mod prime)
setkey ((your-number ^ my-number) mod prime)
end
to make-key-turtles
if not (key = 0)
[crt 1
osetc-of (count-turtles - 1) (key mod 256)
setkey (int (key / 256))
make-key-turtles]
end
to encrypt
reset
repeat stop-after
[setxy counter-x counter-y
setcounter 0
repeat (min count-turtles patches-left)
[setx-of counter (counter-x + counter)
if ((counter-x + counter) > screen-edge)
[sety-of counter (counter-y + 1)
setx-of counter ((counter-x + counter) - screen-size)]
setcounter (1 + counter)
wait 0.1]
stamp (pc bitxor color)
setcounter-x (1 + xcor-of (counter - 1))
setcounter-y (ycor-of (counter - 1))
if (counter-x > screen-size)
[setcounter-x (counter-x - screen-size)
setcounter-y (1 + counter-y)]
setpatches-left (patches-left - counter)]
end
to reset
setcounter-x (0 - screen-edge)
setcounter-y (0 - screen-edge)
setpatches-left (screen-size * screen-size)
ifelse ((patches-left / count-turtles) - int (patches-left / count-turtles)) = 0
[setstop-after (patches-left / count-turtles)]
[setstop-after (1 + int (patches-left / count-turtles))]
end
to setup
ca
make-key
make-key-turtles
end
count-turtles and patches-left.